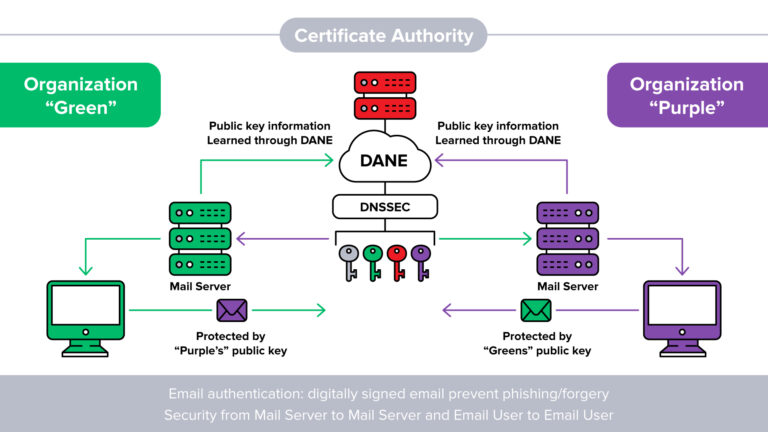
DANE, which stands for “DNS-based Authentication of Named Entities,” is a security protocol designed to enhance the security of the Domain Name System (DNS). The DNS is responsible for translating domain names (such as example.com) into IP addresses, enabling communication between computers over the internet.
Traditionally, the DNS system relies on Transport Layer Security (TLS) certificates to establish secure connections. However, the certificate authority (CA) system, which manages these certificates, has faced security vulnerabilities and instances of trust compromise.
DANE addresses these concerns by allowing domain name owners to directly associate their TLS certificates with their domain names in the DNS records. It leverages DNSSEC (DNS Security Extensions), which provides a secure framework for DNS operations, to store and verify TLS certificate information.
By utilizing DANE, domain owners can assert control over the certificate authority hierarchy, enhancing the security and authenticity of their TLS certificates. It offers a more decentralized and trust-based approach to certificate validation, reducing the reliance on external CAs.
DANE is particularly valuable in mitigating risks associated with CA compromises, such as rogue certificates issued by unauthorized entities or man-in-the-middle attacks. However, it requires DNSSEC deployment and support from both the domain owner and the relying party (e.g., web browsers, email servers) to validate and enforce certificate authenticity through DNS records.
Overall, DANE provides an additional layer of security and control for TLS certificate validation within the DNS infrastructure.