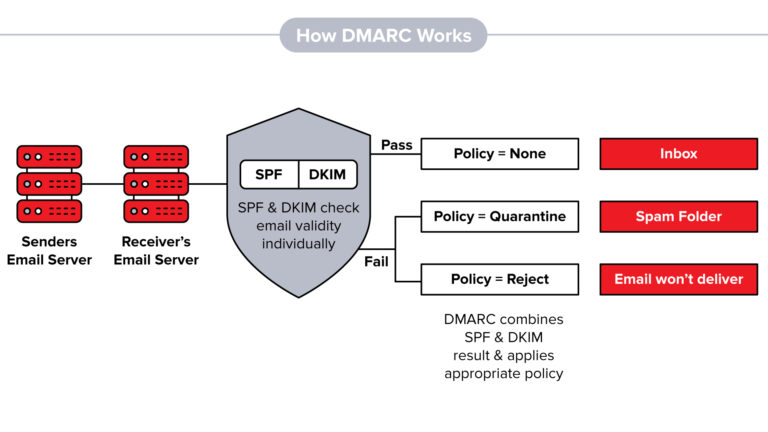
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It is an email authentication protocol designed to combat email phishing and spoofing. DMARC builds upon the existing email authentication protocols, SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), by providing a framework for the alignment of these protocols and specifying how email receivers should handle messages that fail authentication.
The primary goal of DMARC is to protect domain owners from fraudulent use of their domains in phishing attacks. It works by allowing domain owners to publish policies in their DNS records, instructing email receivers on how to handle emails that claim to be from their domain. These policies can be set to monitor, quarantine, or reject emails that fail authentication.
When an email is sent, the receiving server checks for SPF and DKIM records to verify the authenticity of the sender. If both authentication mechanisms pass, the email is considered legitimate. However, if the SPF or DKIM fails, the receiving server checks the DMARC policy published by the domain owner. Based on the DMARC policy, the server can take specific actions such as marking the email as spam, quarantining it, or rejecting it outright.
DMARC also provides reporting capabilities, allowing domain owners to receive feedback on how their domains are being used for email delivery. These reports provide valuable insights into unauthorized use, phishing attempts, and email delivery issues, enabling domain owners to take appropriate measures to protect their brand and reputation.
Overall, DMARC helps prevent email spoofing, protects against phishing attacks, and gives domain owners better control over their email domain’s security. It is widely recommended for organizations and domain owners to implement DMARC as part of their email security measures.